- Screen data inputs for hidden instructions - Our firewall automatically sanitizes tool outputs to block prompt injections before they reach the agent
- Enforce strict role-based access - Control which agents can access which servers, tools, and resources
- Continuous governance through logging - Every interaction is logged with tamper-proof audit trails
- Ringfence sensitive data - Automatically redact PII to prevent leakage from internal LLMs
The Problem
Traditional API gateways and WAFs were not built for MCP. They see HTTP and JSON, but they don’t understand:- MCP methods, tools, resources, prompts, elicitation, sampling, and other protocol primitives
- Multi-step agent flows and how tools are actually used
- Prompt injection and tool poisoning attempts hiding inside “normal” data
What Golf Gateway Does
Govern
Single control point regardless of which agent (Claude, Cursor, ChatGPT, Copilot) employees use.
Audit
Full audit trail for every interaction. Export to your SIEM (Elasticsearch, Sentinel, OTLP).
Control
Centralized RBAC for non-human identities. One policy layer across all your agents and MCP servers.
Protect
Block prompt injections before they reach agents. Sanitize tool outputs and redact PII automatically.
- Without Gateway
- With Gateway
Security
The firewall is the security analysis engine within Golf Gateway.Prompt Injection Detection
The firewall uses an AI model to detect prompt injection attacks in real-time:- Content is extracted from MCP messages (tool arguments, resource content)
- The LLM threat detector analyzes the content
- When the model finds a prompt injection the request is blocked
The model runs locally within the gateway. This ensures low latency and data privacy.
Rate Limiting
Protect against abuse with sliding-window rate limiting at three layers:| Layer | Scope |
|---|---|
| Per-User | Individual user |
| Per-Server | Single MCP server |
| Global | Entire gateway |
Replay Protection
Prevent session token theft and reuse:- When a session is first used, it’s bound to the authenticated user
- If the same session ID appears with a different user, it’s flagged as replay
- Replay attempts are blocked and logged
Audit & Visibility
Every request is logged with cryptographic integrity:- HMAC-SHA256 hash chain - Tamper-evident logging
- Sequence numbers - Detect missing or reordered entries
- Rich metadata - User, server, tool, latency, threat status
Policy Engine
The Policy Engine is the centralized governance system that manages and enforces access control and data protection across Golf Gateway. It operates on a 3-layer hierarchy where policies at each level can restrict (but never expand) permissions:| Policy | Purpose | Hierarchy |
|---|---|---|
| Server RBAC | Control which groups can access MCP servers | All 3 layers |
| Capability RBAC | Control access to tools, prompts, and resources | All 3 layers + annotations |
| PII Scrubbing | Detect and mask sensitive data | All 3 layers |
| Capability Versioning | Require approval for capability changes | Server only |
How Policies Merge
Policies follow a “most restrictive wins” doctrine. As you move down the hierarchy, policies can only become more restrictive, never less:| Field | Merge Rule | Behavior |
|---|---|---|
| Enabled flags | OR | True if ANY layer enables |
| Allowed groups (allow mode) | Intersection | User must be in ALL layers’ groups |
| Denied groups (deny mode) | Union | Blocked if in ANY layer’s deny list |
| Sensitive fields | Union | All fields from all layers are scrubbed |
| Custom rules & entities | Union | Combined from all layers |
Example: Three-Layer RBAC Merge
Example: Three-Layer RBAC Merge
Server RBAC
Server RBAC controls which user groups can connect to each MCP server. Configure at any layer to set defaults or restrictions:| Mode | Behavior |
|---|---|
| Allow (default) | Only users in allowed_groups can access |
| Deny | Users in denied_groups are blocked, others allowed |
Capability RBAC
Capability RBAC provides fine-grained access control for individual tools, prompts, and resources. It uses a 4-layer merge that incorporates MCP tool annotations:Organization Policy
Set default groups for each annotation category (read-only, destructive, unspecified)
Tool Annotations
Annotations are metadata hints that MCP servers provide about their tools. They’re part of the MCP specification and describe the nature of each tool’s behavior—whether it only reads data, makes destructive changes, or falls somewhere in between. Golf Gateway discovers these annotations automatically when it connects to an MCP server and uses them to apply the appropriate access policy:| Annotation | Meaning | Policy Category |
|---|---|---|
readOnlyHint: true | Tool only reads data, no side effects | Read-only |
destructiveHint: true | Tool may perform destructive operations (delete, overwrite) | Destructive |
| Neither annotation | Tool behavior is unspecified or mixed | Unspecified |
Example: Annotation-Based Policy
Example: Annotation-Based Policy
You configure these defaults at the organization level:When a user invokes a tool:
list_files(readOnlyHint: true) → Allowed for all usersdelete_file(destructiveHint: true) → Requires admin groupsend_message(no annotations) → Requires developers or admins
PII Scrubbing Policy
PII scrubbing configuration follows the same 3-layer merge. At each layer you can configure:- Sensitive fields: Field names to always mask
- Pre-built recognizers: Toggle built-in entity detection (21 types)
- Custom rules: Regex patterns with mask/remove/hash/replace methods
- Custom entities: AI-powered detection for custom data types
Capability Versioning
Unlike RBAC and scrubbing policies, versioning is configured per-server only and is not part of the 3-layer policy hierarchy.
- Gateway discovers new/changed capabilities during refresh
- Changes are marked as “pending approval”
- Capabilities are blocked until an admin approves them
- All changes are recorded in the capability history for audit
Authentication
Golf Gateway implements a proxy authentication model: users authenticate to the gateway once, and the gateway manages credentials for upstream MCP servers.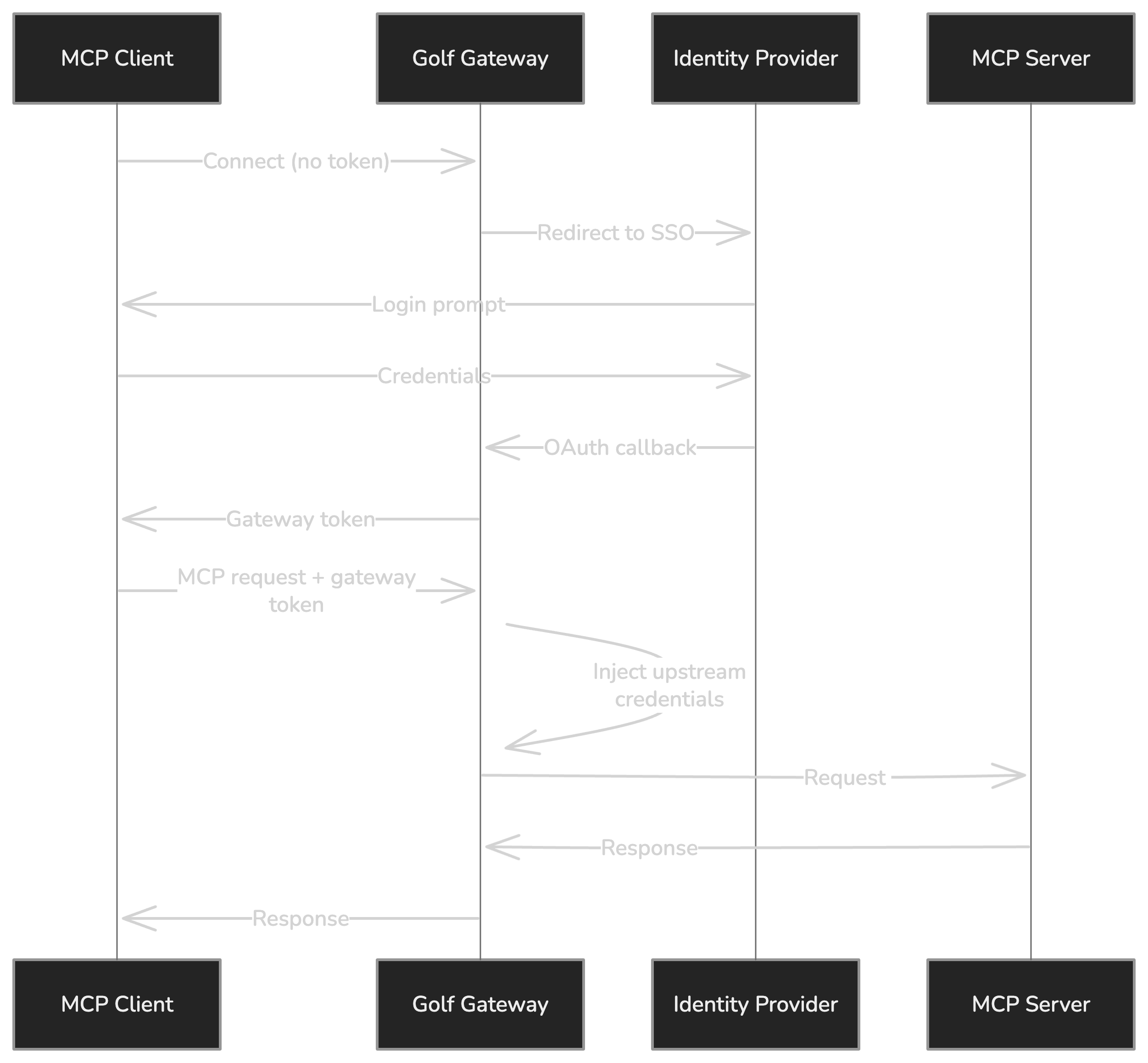
- User authenticates to Gateway via your identity provider (Auth0, Entra ID, Descope)
- Gateway issues a session token (HS256 JWT) for subsequent requests
- Gateway injects upstream credentials for each MCP server the user accesses
- Users never see upstream credentials - they’re managed entirely by the gateway
- API Keys
- OAuth Tokens
For MCP servers that accept static API keys:
- User provides their API key once in the Dev Portal
- Key is encrypted and stored securely
- Gateway injects the key into requests automatically
Configuration Modes
Golf Gateway supports two primary configuration modes that determine where configuration and policies are loaded from:- Centralized Mode
- Distributed Mode
All configuration from Control Plane
- MCP servers, policies, and exporters defined in Control Plane UI
- Gateway fetches configuration bundles on startup and heartbeat
- Hot reload on configuration changes (no restart needed)
| Configuration | Centralized | Distributed |
|---|---|---|
| MCP server definitions | Control Plane | YAML file |
| Server-level RBAC | Control Plane | YAML file |
| Gateway-level policy | Control Plane | YAML file |
| Exporters | Control Plane | YAML file |
| Org-wide policies | Control Plane | Control Plane |
These modes are not mutually exclusive. You can run some gateways in centralized mode and others in distributed mode within the same organization. All gateways share organization-wide policies from the Control Plane.
- Control Plane URL + YAML file → Distributed mode
- Control Plane URL only → Centralized mode
| Mode | Trigger | Latency |
|---|---|---|
| Centralized | Config version change on heartbeat | ~30 seconds |
| Distributed | File system change detected | ~1 second |
When to Deploy Multiple Gateways
Just as organizations deploy multiple API gateways for different domains and audiences, Golf Gateway supports multi-gateway architectures. Each gateway can serve a specific purpose while reporting to the same Control Plane for unified visibility.- Per-Domain
- Per-Audience
- Per-Environment
Separate gateways for different business domainsEach team or department gets its own gateway with tailored policies:
- Engineering Gateway - Company-built agents accessing internal APIs
- HR Gateway - Employee-facing agents with strict PII controls
- Finance Gateway - Agents accessing financial systems with enhanced audit requirements
Benefits
| Benefit | Description |
|---|---|
| Blast Radius Isolation | Issues in one gateway don’t affect others |
| Tailored Policies | Different security requirements per domain or audience |
| Independent Scaling | Scale high-traffic gateways without over-provisioning others |
| Team Autonomy | Teams can manage their own gateway configuration (in Distributed mode) |
| Unified Visibility | Single Control Plane for cross-gateway analytics and audit |
Start with a single gateway and add more as your requirements grow. The Control Plane makes it easy to manage any number of gateways from one place.
Deployment
Golf Gateway is available as Docker images optimized for different hardware configurations.Image Variants
| Variant | Tag | Hardware | Use Case |
|---|---|---|---|
| Core | v1.0.0 | CPU only | Quick tests, POC, cost-sensitive deployments |
| Full | v1.0.0-gpu | NVIDIA GPU | Production with high throughput or advanced PII needs |
Choosing the Right Image
- CPU Image
- GPU Image
Best for: Testing, POC work, and cost-sensitive deployments
- LLM threat detection runs on CPU using a GGUF quantized model
- Works on any infrastructure without special hardware
- Quick testing and evaluation
- Proof-of-concept deployments
- Development environments
- Standard workloads where latency isn’t critical
Hardware Requirements
- CPU Deployment
- GPU Deployment
Recommended:
- 16 vCPU
- 32 GB RAM
c7a.4xlargeRequired Dependencies
Golf Gateway requires the following external services:| Service | Purpose | Notes |
|---|---|---|
| Redis | Session management, rate limiting, replay protection, auth token caching | Required. Redis 7.x recommended. |
Redis is essential for Golf Gateway operation.